The PoINT Storage Manager provides the ideal software-based solution to rising demands for speed, availability, capacity and cost pressures. As well as taking a file’s life cycle into account, the three-level tiered storage architecture of the PoINT Storage Manager also uses the ideal storage technology for each stage of the cycle.
Information Lifecycle Management (ILM)
The value of files and information has been constantly increasing in recent years. One reason for this is increasing demand for storage system stability. Meanwhile, the value of data changes with time, which means that the requirements for the hardware supporting it change as well. As a rule, files can be moved from primary storage to a lower tier after just 30 days and archived after another 60.
The storage and data management solution PoINT Storage Manager takes into account the fact that up to 80% of unstructured data is inactive, meaning that it can be moved from the primary storage system to a lower storage tier (secondary storage) for long-term archiving.
And finally – do you know how much data on your storage system is inactive? The PoINT File System Analyzer provides you with a free software tool to shed some light on your primary storage.
File Archiving and File Tiering
With the help of custom-built policies, files can be efficiently managed as part of the file archiving and tiering processes in the PoINT Storage Manager. Storage capacity is also used as efficiently as possible. Both operational and legal compliance are implemented and ensured. Optimizing storage resources and flexibly integrating developer-independent storage technology helps to avoid cost-intensive expansion of high-performance primary storage. This allows the PoINT Storage Manger to meet current business-specific demands.

"We were convinced by the concept of the PoINT solution. By implementing PoINT Storage Manager we could not only reduce our costs for storage extensions considerably but also fulfill our archiving obligations. Especially the easy and homogeneous integration of secondary storage systems into our existing infrastructure without any changes for users nor applications was crucial."
- Thomas Weber, Head of IT, e.solutions GmbH
PoINT Storage Manager – flexible and efficient
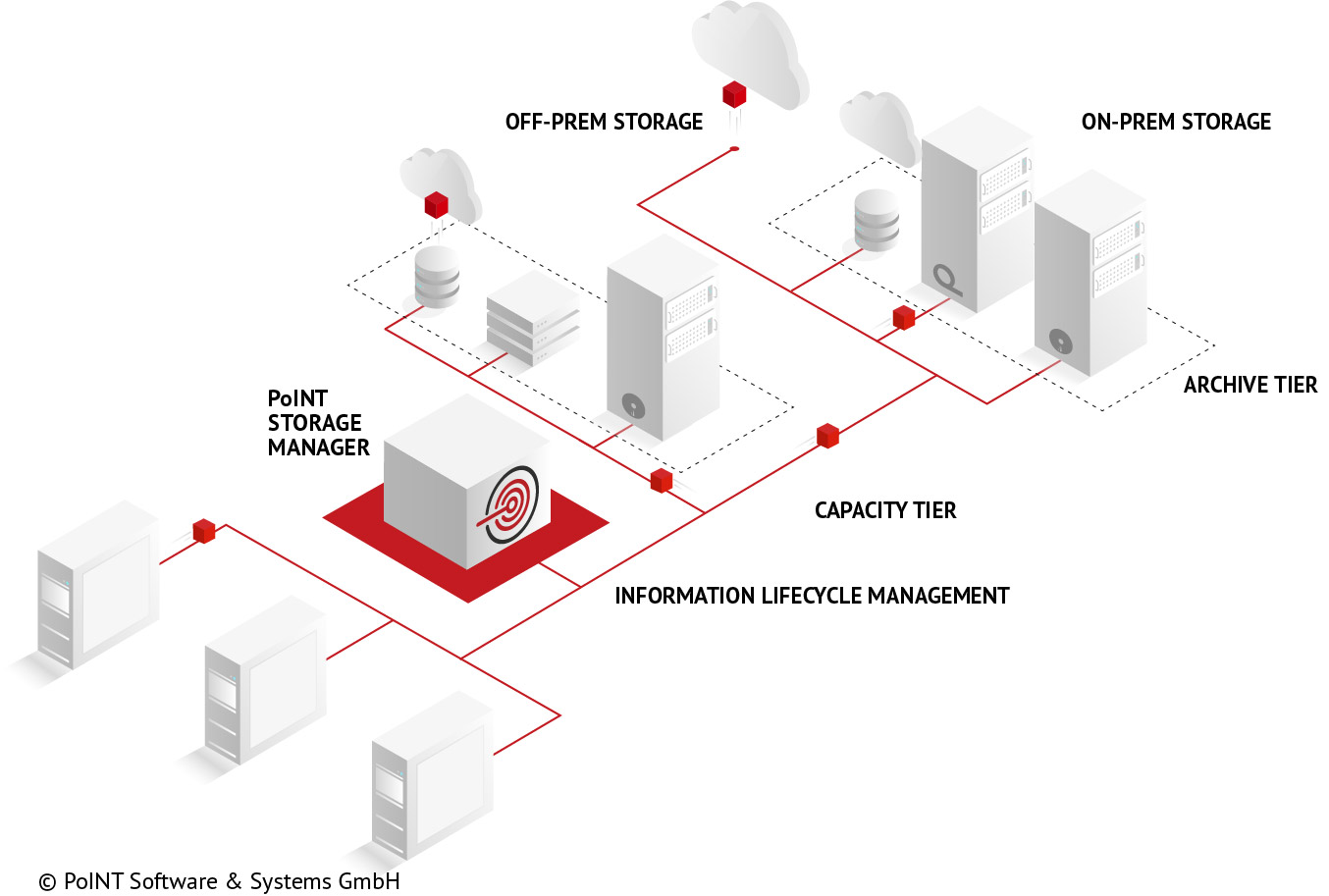
The PoINT Storage Manager demonstrates particular flexibility in its range of supported target storage systems. All available technologies (e.g. cloud and object storage, tape, etc.) can be used without requiring any additional software. Using the replication function enables additional system security thanks to the use of diverse technologies across multiple locations.
Using the PoINT Storage Manager and combining a range of storage systems and custom-tailored policies within a tiered storage architecture can substantially reduce procurement and operational costs for management and backup processes.
Properties
File Archiving and Tiering
When you consider the lifecycle of a file, it becomes clear that the challenges relating to manageability and performance vary when moving from one cycle to another. A multi-tiered storage architecture can both meet files’ requirements and also integrate the required hardware to make optimal use of it.
The storage vault concept can configure up to 64 individual archiving and storage transfer processes with individually specified policies. The single-point-access approach through the primary storage system (source system) enables transparent archiving and data transferal for users and applications. There is no need to make any adjustments to the existing workflow.
Transparent read access for the PoINT Storage Manager is enabled through the use of so-called “stubs”, reducing unnecessary re-storage of inactive or archive-ready data. However, policies can help to automatically retrieve files that have once again become relevant.
The multi tiered storage architecture of the PoINT Storage Manager allows the use of a range of storage technologies without requiring any additional software. With the help of policies, inactive and archive-ready files are automatically archived and transferred to more suitable, more cost-effective secondary storage. As well as reducing the amount of primary storage required, this automatic process also leads to increased efficiency in working processes and optimized operational efficiency.
File archiving allows businesses to meet both internal and legal compliance requirements, taking into account the relevant requirements for files. The flexible “write once, read many” (WORM) properties of the PoINT Storage Manager create the foundations for compliance.
Retention Management
Retention management enables targeted, time-specific protection of archived files against manipulation, changes or deletion. In many industries, this represents the foundation for compliance with legal regulations on storage periods. Once the retention period expires, files can be selectively chosen and both the stub in primary storage and the archived file in secondary storage can be deleted. Retention management also enables management and maintenance of archived files. After a specified period of time, archived files without stubs (a link to the primary storage system) can be marked and selected for deletion.
Versioning of archived files can be configured based on rules for how multiple versions should be preserved.
Replication
The flexibility of a multi-tiered storage architecture enables both the storage and archiving of data as well as rules-based replication across additional secondary storage systems within a given tier. Replication of this type can enable both geographical and technological separation. Under this system, the so-called archive tier can be configured to include up to four different archive storage systems and technologies, enabling extremely high system stability.
Integrating Cloud and Object Storage
Cloud storage and object-based storage systems (object storage) can be used on a targeted basis thanks to the flexible properties of the multi-tiered storage architecture used within the PoINT Storage Manager. They can be integrated into storage infrastructure using a standard file system, making the concept easy to execute. Storage virtualization within (private) cloud storage can help to balance out issues such as peak demand across separate departments or applications. Public cloud storage services (from a cloud storage provider) should be preferred for archiving in the archive tier or for replicating locally archived files. Replication is used in a targeted fashion to increase system stability.
Authentication also offers additional data security. Manipulation and misuse are also covered. The use of an AES256- and CBC-based block-level encryption process guarantees additional protection for data.
The flexible multi-tiered storage architecture opens up the option for customers to use a hybrid cloud storage infrastructure (a combination of public/private cloud storage and traditional storage technologies) in order to benefit from the specific advantages of each chosen option and to optimize storage.
PoINT Storage Manager can use corresponding connectors to integrate the standard S3 and CDMI interfaces as well as the following object-based storage systems (object storage):
- Amazon S3
- Caringo CAStor / Swarm
- Cloudian HyperStore
- DellEMC Atmos / ECS
- DellEMC Centera
- HGST Active Archive
- Hitachi Content Platform
- IBM COS
- Microsoft Azure
- NetApp StorageGRID Webscale
- Quantum Lattus
- Scality RING
- SUSE Enterprise Storage
Migrating Primary and Secondary Storage
Businesses are increasingly facing the challenge of dismantling outdated storage systems within their IT infrastructure and moving to new ones. With the help of the PoINT Storage Manager, the integrated PoINT VFS can integrate outdated systems (e.g. MO/WORM jukeboxes) and new ones into a consolidated storage solution. The files from the old storage system remain accessible to the file system during data migration and are seamlessly transferred across to the new storage system in the background. This transparent scenario enables uninterrupted application operations, even during data migration, and avoids the need for reconfiguration. This also reduces the need to retain excessively costly support contracts with the sole purpose of keeping outdated hardware on life support. The tiered storage architecture can be realized on benefit-oriented hardware components with the help of transparent data migration, resulting in an optimal solution for the user.
This integrated migration functionality produces significant planning security and flexibility for businesses in terms of storage technology and hardware. The tiered storage architecture means that files can be stored on a suitable storage level at any time based on their value, and it also makes future technological updates easy to implement.
However, the migration concept is not only useful for archiving systems – it is also suitable for migrating primary storage systems. With the help of the PoINT Storage Manager Agents for NetApp FAS, EMC VNX and Windows NTFS, primary storage systems from leading hardware manufacturers can be transparently migrated to a new system without any interruptions.
Data Protection & Security
The PoINT Storage Manager provides network-wide, rules-based data security which can be implemented even within complex internal business infrastructures. Reliable data security is essential both for protecting sensitive data and for compliance purposes. Automated, transparent data replication allows data to be secured redundantly on configured storage systems, avoiding data loss through forward planning. The parallel use of varying storage technologies, with each of their respective advantages, forms another component of the data protection plan. The use of removable media and the integration of cloud storage into a three-tier storage architecture enables data protection through geographically separated off-site storage. Recovery support enables optional setup of the storage environment , rounding out the data protection package.
Aside from data protection, data security is also a critical component for securely working with business data. The data security system uses an AES256- and CBC-based block-level encryption process, and the storage configuration itself can also be secured using a unique encryption key.
Another component of data security is the data authenticity function based on the SHA-1 standard. The automatically calculated hash value enables data authenticity to be checked in order to identify potential manipulation of archived data.
User Controlled Archiving
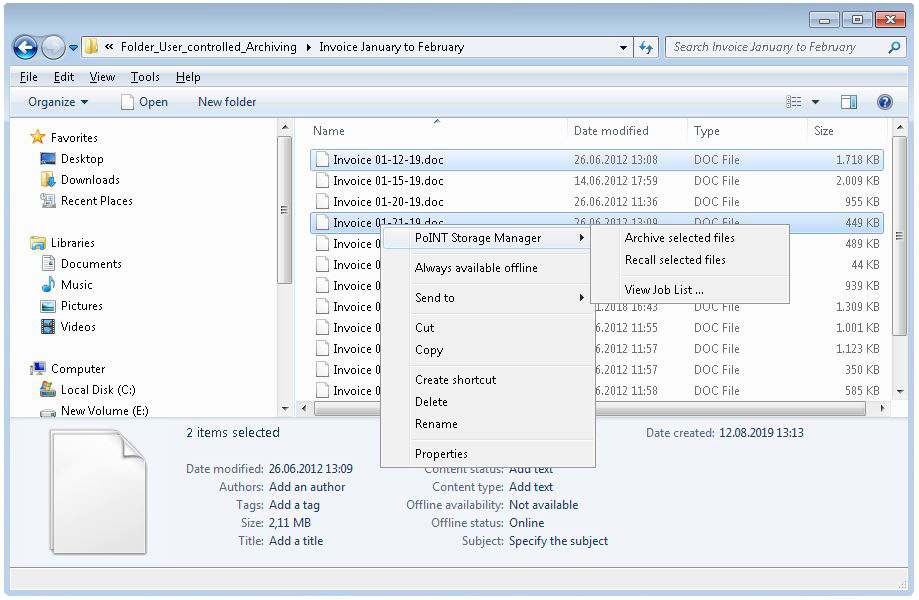
This feature enables users to manually initiate archiving of selected data themselves. The administrator provides a framework of rules and commands and authorizes the users. The users can then select the “User Controlled Archiving” feature via the familiar user interface of the Windows Explorer. So there is no need to familiarize with a new software or interface. Thus users can easily archive files and, if necessary, restore them.
Benefits and Advantages
- Efficiently use primary storage by transferring and archiving inactive data (data migration)
- Fast, standardized access to all data
- Automation reduces management work
- Use applications without interruption
- Save time and money by reducing backup data volumes and making optimal use of primary and secondary storage
- Meet compliance requirements
- No additional software required to integrate tape and optical storage
Technical Information
Solution Briefs
Source & Target Systems
Here you can find information for the source systems.
Target systems:
NAS (Dell/EMC, HP, NetApp, Fujitsu, …)
Object-based Storage (Cloudian, Dell/EMC, HDS, NetApp, IBM, Scality, SUSE…)
Public Cloud Services (Amazon, Microsoft, …)
Appliances (Crossroads, FAST LTA, NetApp, …)
Tape (HP, IBM, Quantum, Qualstar, Spectra, ...)
Optical (Dacal, DISC, HIT, SONY, …)
Here you can find additional information for the target systems.
System Requirements
Here you can find information for the system requirements.
Tutorials

Under the following links you find tutorials which support you with the configuration of PoINT Storage Manager:
- Tutorial 1: Installation >>>
- Tutorial 2: Configuration >>>
- Tutorial 3: Archive Device Configuration >>>
- Tutorial 4: Storage Vault Configuration >>>
- Tutorial 5: Policy Configuration >>>
- Tutorial 6: Archive Device Migration >>>
- Tutorial 7: Recovery Policies & Data Browser >>>
- Tutorial 8: Data Authentication >>>